Program development > C# > Content
Program development > C# > ContentThe RSA key container could not be opened(System.Security.Cryptography.Utils.CreateProvHandle)
In the website developed by Asp.net, the information in Web.config(especially the string connecting to the database) is in plain text. It is easy to expose the database name, login user name and password, so sensitive information must be encrypted. .Net provides RSA encryption, which can be used to complete the encryption of Web.config.
Encrypted Web.config is safe, but it is also prone to problems. For example, RSA encryption can only be decrypted on the local machine. After the website is migrated, it cannot be decrypted again unless the key is exported and imported to the migrated server. There is also a common problem: The RSA key container could not be opened.(System .Security.Cryptography.Utils.CreateProvHandle), for this problem, sometimes setting a folder permissions is solved, sometimes it doesn't work, and it is still a bit troublesome to solve it.
Solution of the RSA key container could not be opened(System.Security.Cryptography.Utils.CreateProvHandle)
1. This problem is mostly caused by the lack of read and write permissions to the folder MachineKeys, so only the "Read and Modify" permissions are assigned to it, and the problem can be solved. The steps are as follows:
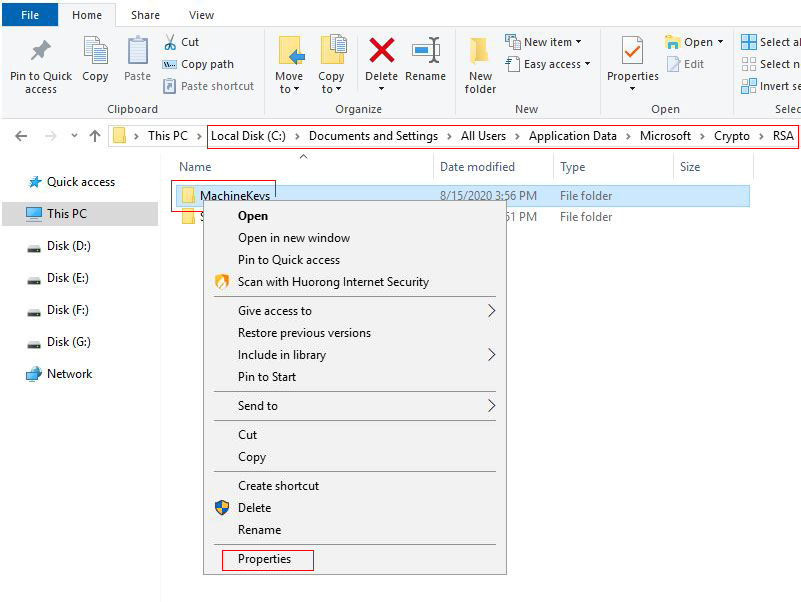
A. Open the C:\Documents and Settings\All Users\Application Data\Microsoft\Crypto\RSA folder, right-click the MachineKeys folder and select "Properties", as shown in Figure 1:
Figure 1
B. In the opened "MachineKeys Properties" dialog box, select the "Security" tab, as shown in Figure 2:
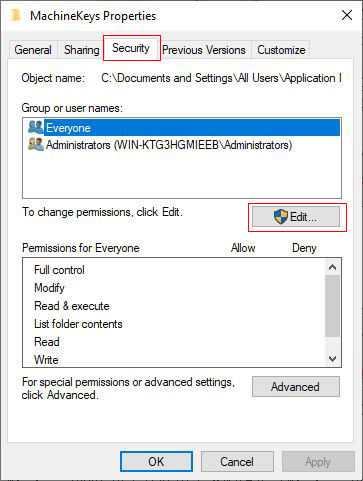
Figure 2
C. Windows server 2008 and above, click "Edit"(Windows server 2003 is not necessary), and open the permission dialog box as shown in Figure 3:
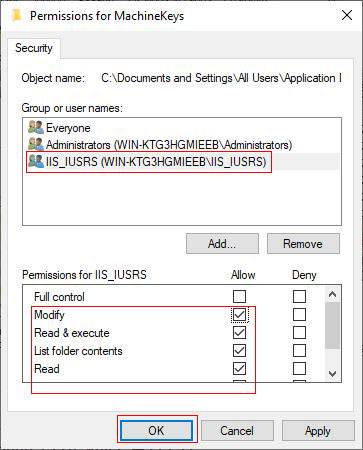
Figure 3
D. Add the IIS_IUSRS user in Windows server 2008 and above systems, and add the IIS_WPG user in Windows server 2003, and assign the "Read and Modify" permissions to it; generally speaking, when the key is generated(when encrypting), give the "Modify" permission, when decrypt Only "Read" permission is required.
Add IIS_IUSRS(IIS_WPG) user:
Click "Add" in Figure 3 → Advanced → Find Now → double-click the IIS_IUSRS(IIS_WPG) user in the "Search Results" → OK.
2. If adding the "Modify" permission to the MachineKeys folder does not work, you can change the "predefined user" to "local system" in the IIS application pool(note: to reduce security), the steps are as follows:
Windows server 2003:
"Start" menu → Administrative Tools → Internet Information Services → expand "Application Pools" under "Internet Information Services" → right-click "Application Pool(such as DefaultAppPool)" → Properties → "Identity" tab → Select "Local System" for "Predefined User".
Windows server 2008 and above:
"Start" menu → Windows Administrative Tools → Internet Information Services (IIS) Manager → expand "Application Pools" under "your computer name" → right-click "Application Pool(such as DefaultAppPool)" → Set Application Pool Defaults → select "Identity", click button its right → Select "Local System", as shown in Figure 4:
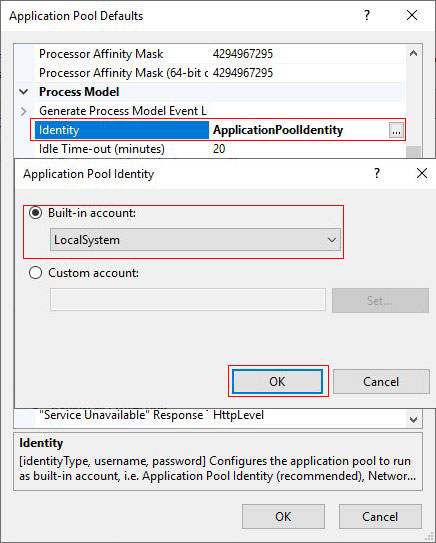
Figure 4
-
Related Reading
- C# listview select row(a row and multiple rows)
- Solve the flickering problem of C# listview multithr
- C# convert punctuation marks to Unicode encoding
- C# Read and write to text file Newline, with one lin
- C# merge binary array(byte array)
- C# Winform button transparent background with proper
- Convert Unicode to string C#(with string to unicode)
- C# set Winform icon and version number
- C# float, double range, precision, definition and ty
- C# split string with \n pay attention to the problem
- C# efficiency comparison of multiple strings concate
- C# date format and examples, with binding and ToStri